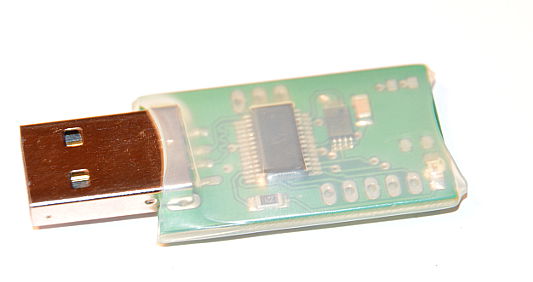
USB RAM drive stick for dm-crypt/luks partitions (or other crypto setup)
Storing key/password files on the common removable media like USB flash drives is not secure - device may be removed from the USB
port and its contents will be disclosed. USB RAM drive stick is differ - it retains its contents only when plugged into USB port.
This device is a compromise between the advantages of the use of the encrypted disks/partitions
and secure auto-mounting them (dm-crypt or others) without interactively entering password/keyfile on each reboot/restart.
Most PCs and servers provide stable power to the USB port even during poweroff state, so USB RAM drive stick retains its contents when
PC is powered off (PC power supply is in standby mode). When power is completely off (hardware "off" switch on the power supply or mains was removed) USB RAM drive stick lost
its contents and password file(s) must be rewritten.
WARNING
For prevent unauthorized boot to other OS and disclose USB RAM drive stick contents PC BIOS must be protected with the password and
configured to boot only from the main hd without any alternate boot device. Bootloaders (Grub, Lilo etc.) must be secured to prevent boot to a single user
mode or change/modify boot options like init= (like init=/bin/bash)
WARNING
Device features:
- device is detected by any OS (Linux/Windows/MAC) as a regular USB removable drive formatted with FAT
- device doesn't contain any permanent storage (like flash memory), files are stored only in device ram memory.
- 128kB free for the key/password file(s)
- contents on the stick is permanently destroyed after unplugging it from the USB port
- after each plugging into USB port device's internal ram is zeroed, FAT is recreated so any previous content will be deleted.
- contents retains durning PC power on/off (when plugged in USB port with some limitations) and reboots - no need to re-enter the password after each boot/restart (with special init script - details below in HOWTO)
|
|
USB RAM drive stick MINI HOWTO for Linux Debian (or compatible) with dm-crypt
The following instructions do not explain how prepare, format and mount dm-crypted partitions. They assume that you already have experience
with working dm-crypt setup and you always enter the password(s) on each boot/restart for mounting encrypted partitions. To learn how use dm-crypt
please refer to the dm-crypt documentation (man cryptsetup).
USB RAM stick preparing & mounting instructions:
- insert the USB RAM drive stick into the USB port, wait for detection
- create "tc" dir in /:
# cd /; mkdir tc
- secure mount /tc dir with detected USB RAM disk (in the following example /dev/sdc1 is the detected USB RAM device):
# mount -o umask=277 /dev/sdc1 /tc
- create /tc/key file which contains dm-crypt password, make sure there is no newline at the end, some text editors like vim usually adds an extra new line character, you have to strip it from the key file.
- you need two cryptab files for replacing /etc/cryptab contents when password file is not available. These files are required by
tcryptdisk init script described below. First copy your original /etc/crypttab to /etc/crypttab_p
# cp /etc/crypttab /etc/crypttab_nop
now create the another copy:
# cp /etc/crypttab /etc/crypttab_p
Now edit /etc/crypttab_nop and replace column contains "none" (no key file) with "/tc/key".
- install tcryptdisk init script file in /etc/init.d/ dir
Now you can verify auto-mounting dm-crypt partitions during boot. Init script tcryptdisk try mount /tc if USB RAM drive stick is detected.
If /tc/key file exits (and contains proper password) encrypted
partition(s) will be auto mounted. If the key file is not available (USB stick was removed or PC mains was switched off) auto-mounting
script will ask on the console for the password and you have to re-create key file as described above.
Remember secure BIOS as described in the warning above.
|
|
|
The USB RAM stick is avialable on eBay.
For any questions or ordering informations please use the contact form in the page header.
|
